Root access exploiting a kernel bug
May 14, 2008
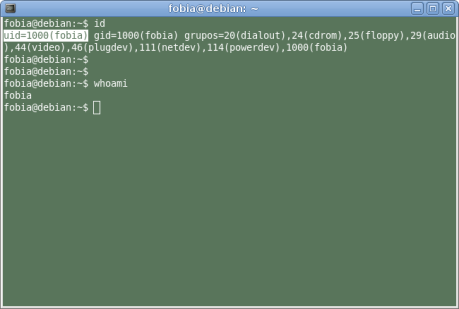
The uid and gid have a little bug that allow users being root, obviously it’s not that simple, the source code in the exploit(written in C and Assembler) let you have access as root, without asking for a password, this bug can be great if you wanna hack a system, but for the ones that want protect their system it’s a really huge problem.
It can be fixed, the bug just can be exploited in 2.6.24.1 kernel and olders, actually, if you got a newer kernel you don’t have to be afraid.
Well you just have to compile and run the program, but it will be great if you understand the source code, the bug was improved from an older version, anyway, it works really good, here you have a couple of screenshots.
if you want the code, write a comment and i’ll mail you.
Root shell from grub
May 13, 2008
Well now, I’ll show you a trick to get root access without any password, from the grub it’s pretty simple, we’ll get access like recovery mode, and that will give us the root shell, just by modifying one line.
When the grub boots, type ‘e’ to edit the line that boots linux, then you’ll see some lines, edit the line that contains the kernel, then somewhere you’ll se ‘ro quiet’ or something like that, then erase from the end until the ro and edit to
ro init=/bin/bash
bash is the shell we want, it can be csh or sh.
Then press return and you’ll return to the lines of the grub in your linux choice, DON’T TYPE RETURN TO BOOT, BECAUSE THE TRICK WON’T WORK, YOU HAVE TO TYPE ‘b’ TO BOOT WITH THE LINE WE CHANGED, then you’ll have the root access.
Here’s the video hos this works.
Enjoy it